Introduction
In this write-up, we walk through levels 6 to 10 of OverTheWire's Bandit wargame.
Level 6 -> 7
Link to level 6.
The Goal
The password for the next level is stored somewhere on the server and has all of the following properties:
- owned by user bandit7
- owned by group bandit6
- 33 bytes in size
Finding The Password
Let's start by using SSH to login to the box...
sshpass -p <level-6-password> ssh bandit.labs.overthewire.org -p 2220 -l bandit6
This level expands on the previous by introducing the idea of file ownership and redirection of output. Time for a quick explanation:
Files and folders all have a user and a group assigned to them; these tie into file permissions, which we'll touch on later. But for now, know that both of these dictate who can do what with a given file or folder.
To find this file, we must use the clues we've been given. This shouldn't be too hard with the following command:
find / -user bandit7 -group bandit6 -size 33c
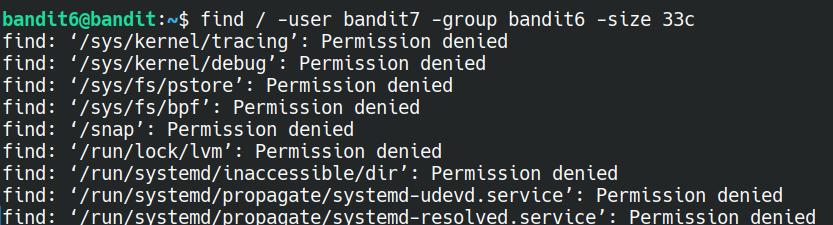
Oh dear, we have a lot of text on the screen stating Permission denied. What does that all mean? Put simply, we don't have permissions to view these files; we're either not the assigned user or in a group that has the rights to perform certain actions.
All of the errors are being printed out to one of the standard streams known as stderr. The standard streams would take too long to explain in this little write-up, so more information can be found here.
Lucky for us, we're able to "filter" out or redirect these errors to a special place known as /dev/null. /dev/null is effectively a blackhole where any data that enters it is lost forever. To utilise this, we need to add 2> /dev/null to the end of our command.
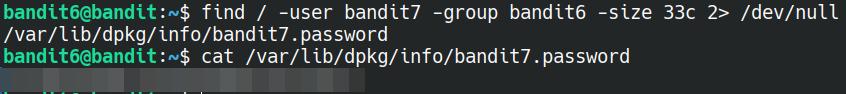
find / -user bandit7 -group bandit6 -size 33c 2> /dev/null
With all of the noice removed, we are able to see the password for the next level is located in the file /var/lib/dpkg/info/bandit7.password.
Level 7 -> 8
Link to level 7.
The Goal
The password for the next level is stored in the file data.txt next to the word millionth
Finding The Password
Let's start by using SSH to login to the box...
sshpass -p <level-7-password> ssh bandit.labs.overthewire.org -p 2220 -l bandit7
Straight off the bat, we are able to see a file in the user's home directory with the name in the spec. If we were to cat the file out to the command line, we would see a whole lot of text stream past our screens; 98567 lines to be exact. So, how do we find the password to the next level?
This is where our friend grep comes in. grep is a command line utility that can find strings of text based on some search pattern. It supports regex, but we won't be needing anything that fancy here.
The command we can use for this is:
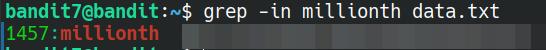
grep -in millionth data.txt
The options used in this are -i to make the search case insensitive so that it doesn't matter if there's a mixture of uppercase and lowercase characters, and -n to print out the line number any results were found on (not necessary for this, but fun to know).
Level 8 -> 9
Link to level 8.
The Goal
The password for the next level is stored in the file data.txt and is the only line of text that occurs only once
Finding The Password
Let's start by using SSH to login to the box...
sshpass -p <level-8-password> ssh bandit.labs.overthewire.org -p 2220 -l bandit8
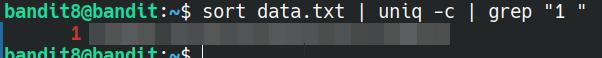
Just like the previous level, the file we need for finding the password is sitting in the user's home directory, and using cat, we can see approximately 1000 lines of text. To find the password, we'll need to use a couple of commands: sort and uniq. It is possible to use sort with the -u option to print out all of the unique strings, but it doesn't have the capability to print the number of times that string has appeared in the text, unlike uniq.
The command to use for this is below:
sort data.txt | uniq -c | grep "1 "
Level 9 -> 10
Link to level 9.
The Goal
The password for the next level is stored in the file data.txt in one of the few human-readable strings, preceded by several = characters.
Finding The Password
Let's start by using SSH to login to the box...
sshpass -p <level-9-password> ssh bandit.labs.overthewire.org -p 2220 -l bandit9
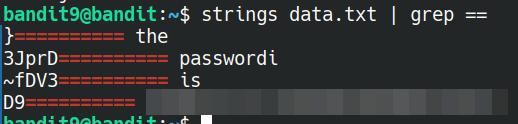
Taking a look at the file given to us using cat, we're presented with some interesting data that isn't totally human-readable. Luckily, there exists a command that will print out only the human-readable parts of the file, and that is the strings utility.
By itself, it isn't too much use, as it will find anything that is a minimum of 4 characters in length that contains readable ASCII characters. So we'll need to pipe this into grep. We know from the information given to us, we just need to search for multiple = symbols. Using the following command, we're able to get the password for the next level:
strings data.txt | grep ==
Level 10 -> 11
Link to level 10.
The Goal
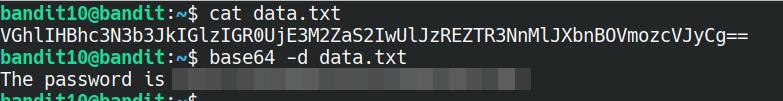
The password for the next level is stored in the file data.txt, which contains base64 encoded data
Finding The Password
Let's start by using SSH to login to the box...
sshpass -p <level-10-password> ssh bandit.labs.overthewire.org -p 2220 -l bandit10
The hint for this level is that the data is encoded using base64. More information on what base64 is can be found here.
And again, lucky for us, there's a command line utility that can help us decode the string contained within the file: base64. We're able to use the -d flag to decode the data.
base64 -d data.txt